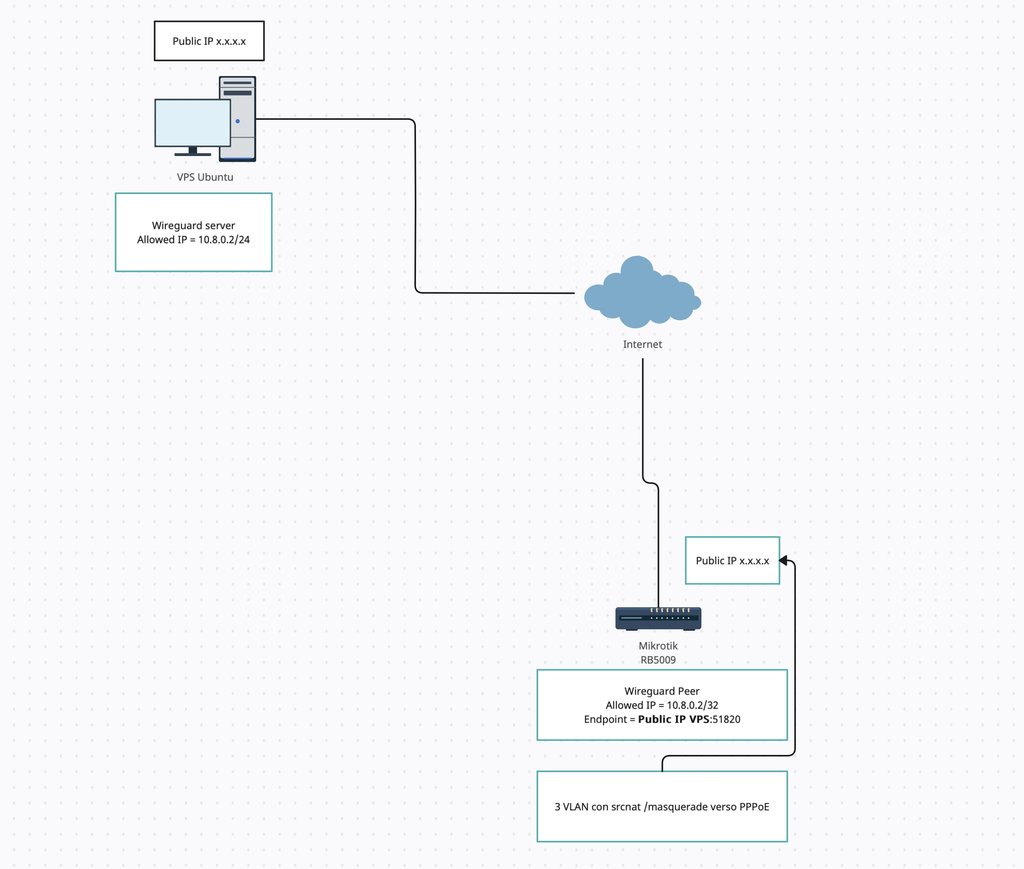
Ciao a tutti, è da un paio di giorni che sto smanettando per capire come configurare il mio Mikrotik RB5009 come peer tramite Wireguard con una macchina VPS Ubuntu che è configurata come server.
Ho già configurato la VPS con Wireguard correttamente seguendo una guida online ma ho dei problemi col mio Mikrotik in quanto non riesco a impostare correttamente le regole del firewall, NAT e Routing.
Quello che vorrei fare è inoltrare il traffico della mia rete verso la VPS in modo tale da accedere ad un tool di monitoraggio che ho installato senza dover utilizzare il reverse proxy. In passato sono riuscito a configurare correttamente la VPN come server sul mio mikrotik per accedere da remoto dai miei dispositivi. In questo caso però che deve fare da peer sbaglio qualcosa.
Qui di seguito vi allego uno schema di quello che vorrei fare giusto per avere un'idea più precisa e anche la mia configurazione attuale. Per configurare inizialmente il firewall ho letto proprio la wiki di Mikrotik appena ho comprato il router e ho seguito i loro suggerimenti.
Oltre che chiedere una mano, siccome sono interessato alla questione del networking mi piacerebbe capire il perché utilizzare certe regole così imparo qualcosa.
Grazie in anticipo!😀
/interface vlan
add interface=ether1 name=VLAN_DIMENSIONE vlan-id=835
add interface=ether5 name=VLAN_Home vlan-id=30
add interface=ether5 name=VLAN_IoT vlan-id=10
add interface=ether5 name=VLAN_WIFI_GUEST vlan-id=20
/interface pppoe-client
add add-default-route=yes dial-on-demand=yes disabled=no interface=VLAN_DIMENSIONE keepalive-timeout=disabled name=pppoe_dimensione user=
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/ip pool
add name=default-dhcp ranges=192.168.88.10-192.168.88.254
add name=dhcp_pool1 ranges=192.168.10.2-192.168.10.254
add name=dhcp_pool2 ranges=192.168.20.2-192.168.20.254
add name=dhcp_pool3 ranges=192.168.10.2-192.168.10.254
add name=dhcp_pool4 ranges=192.168.20.2-192.168.20.254
add name=dhcp_pool5 ranges=192.168.10.2-192.168.10.254
add name=dhcp_pool6 ranges=10.0.20.2-10.0.20.254
add name=dhcp_pool7 ranges=10.0.10.10-10.0.10.100
add name=dhcp_pool8 ranges=10.0.30.2-10.0.30.254
/ip dhcp-server
add address-pool=default-dhcp interface=bridge name=defconf
add address-pool=dhcp_pool6 interface=VLAN_WIFI_GUEST name=DHCP_WIFI
add address-pool=dhcp_pool7 interface=VLAN_IoT name=DHCP_IoT
add address-pool=dhcp_pool8 interface=VLAN_Home name=DHCP_Home
/snmp community
set [ find default=yes ] addresses=0.0.0.0/0
/interface bridge port
add bridge=bridge comment=defconf interface=ether2
add bridge=bridge comment=defconf interface=ether3
add bridge=bridge comment=defconf interface=ether4
add bridge=bridge comment=defconf interface=ether5
add bridge=bridge comment=defconf interface=ether6
add bridge=bridge comment=defconf interface=ether7
add bridge=bridge comment=defconf interface=ether8
add bridge=bridge comment=defconf interface=sfp-sfpplus1
/ip neighbor discovery-settings
set discover-interface-list=LAN
/interface list member
add comment=defconf interface=bridge list=LAN
add comment=defconf interface=VLAN_DIMENSIONE list=WAN
/interface ovpn-server server
set auth=sha1,md5
/ip address
add address=192.168.88.1/24 comment=defconf interface=bridge network=192.168.88.0
add address=10.0.10.1/24 interface=VLAN_IoT network=10.0.10.0
add address=10.0.20.1/24 interface=VLAN_WIFI_GUEST network=10.0.20.0
add address=10.0.30.1/24 interface=VLAN_Home network=10.0.30.0
/ip cloud
set ddns-enabled=yes ddns-update-interval=1m
/ip cloud advanced
set use-local-address=yes
/ip dhcp-client
add comment=defconf interface=VLAN_DIMENSIONE use-peer-dns=no
/ip dhcp-server network
add address=10.0.10.0/24 gateway=10.0.10.1
add address=10.0.20.0/24 gateway=10.0.20.1
add address=10.0.30.0/24 gateway=10.0.30.1
add address=192.168.88.0/24 comment=defconf gateway=192.168.88.1
/ip dns
set allow-remote-requests=yes use-doh-server=https://dns.nextdns.io verify-doh-cert=yes
/ip dns static
add address=192.168.88.1 comment=defconf name=router.lan
add address=45.90.28.0 name=dns.nextdns.io
add address=45.90.30.0 name=dns.nextdns.io
add address=2a07:a8c0:: name=dns.nextdns.io type=AAAA
add address=2a07:a8c1:: name=dns.nextdns.io type=AAAA
/ip firewall address-list
add address=192.168.88.2-192.168.88.254 list=allowed_to_router
add address=0.0.0.0/8 comment=RFC6890 list=not_in_internet
add address=172.16.0.0/12 comment=RFC6890 list=not_in_internet
add address=192.168.0.0/16 comment=RFC6890 list=not_in_internet
add address=10.0.0.0/8 comment=RFC6890 list=not_in_internet
add address=169.254.0.0/16 comment=RFC6890 list=not_in_internet
add address=127.0.0.0/8 comment=RFC6890 list=not_in_internet
add address=224.0.0.0/4 comment=Multicast list=not_in_internet
add address=198.18.0.0/15 comment=RFC6890 list=not_in_internet
add address=192.0.0.0/24 comment=RFC6890 list=not_in_internet
add address=192.0.2.0/24 comment=RFC6890 list=not_in_internet
add address=198.51.100.0/24 comment=RFC6890 list=not_in_internet
add address=203.0.113.0/24 comment=RFC6890 list=not_in_internet
add address=100.64.0.0/10 comment=RFC6890 list=not_in_internet
add address=240.0.0.0/4 comment=RFC6890 list=not_in_internet
add address=192.88.99.0/24 comment="6to4 relay Anycast [RFC 3068]" list=not_in_internet
/ip firewall filter
add action=accept chain=input comment="defconf: accept established,related,untracked" connection-state=established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment="defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=accept chain=input dst-port=53 in-interface=all-vlan protocol=tcp
add action=accept chain=input dst-port=53 in-interface=all-vlan protocol=udp
add action=drop chain=input comment="defconf: drop all not coming from LAN" in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" connection-state=established,related hw-offload=yes
add action=accept chain=forward comment="defconf: accept established,related, untracked" connection-state=established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" connection-state=invalid
add action=drop chain=forward comment="defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat connection-state=new in-interface-list=WAN
add action=accept chain=input comment="default configuration" connection-state=established,related
add action=accept chain=input src-address-list=allowed_to_router
add action=accept chain=input protocol=icmp
add action=drop chain=input
add action=fasttrack-connection chain=forward comment=FastTrack connection-state=established,related hw-offload=yes
add action=accept chain=forward comment="Established, Related" connection-state=established,related
add action=drop chain=forward comment="Drop invalid" connection-state=invalid log=yes log-prefix=invalid
add action=drop chain=forward comment="Drop tries to reach not public addresses from LAN" dst-address-list=not_in_internet in-interface=bridge log=yes log-prefix=!public_from_LAN out-interface=\
!bridge
add action=drop chain=forward comment="Drop incoming packets that are not NATted" connection-nat-state=!dstnat connection-state=new in-interface=ether1 log=yes log-prefix=!NAT
add action=jump chain=forward comment="jump to ICMP filters" jump-target=icmp protocol=icmp
add action=drop chain=forward comment="Drop incoming from internet which is not public IP" in-interface=ether1 log=yes log-prefix=!public src-address-list=not_in_internet
add action=drop chain=forward comment="Drop packets from LAN that do not have LAN IP" in-interface=bridge log=yes log-prefix=LAN_!LAN src-address=!192.168.88.0/24
add action=accept chain=icmp comment="echo reply" icmp-options=0:0 protocol=icmp
add action=accept chain=icmp comment="net unreachable" icmp-options=3:0 protocol=icmp
add action=accept chain=icmp comment="host unreachable" icmp-options=3:1 protocol=icmp
add action=accept chain=icmp comment="host unreachable fragmentation required" icmp-options=3:4 protocol=icmp
add action=accept chain=icmp comment="allow echo request" icmp-options=8:0 protocol=icmp
add action=accept chain=icmp comment="allow time exceed" icmp-options=11:0 protocol=icmp
add action=accept chain=icmp comment="allow parameter bad" icmp-options=12:0 protocol=icmp
add action=drop chain=icmp comment="deny all other types"
add action=fasttrack-connection chain=forward connection-state=established,related hw-offload=yes
add action=accept chain=forward connection-state=established,related
add action=drop chain=input comment="Drop Port 53 UDP" connection-state="" dst-port=53 in-interface=pppoe_dimensione protocol=udp
add action=drop chain=input comment="Drop Port 53 TCP" connection-state="" dst-port=53 in-interface=pppoe_dimensione protocol=tcp
/ip firewall nat
add action=masquerade chain=srcnat out-interface=pppoe_dimensione src-address=10.0.20.0/24
add action=masquerade chain=srcnat out-interface=pppoe_dimensione src-address=10.0.10.0/24
add action=masquerade chain=srcnat out-interface=pppoe_dimensione src-address=192.168.88.0/24
add action=masquerade chain=srcnat out-interface=pppoe_dimensione src-address=10.0.30.0/24
add action=redirect chain=dstnat dst-port=53 protocol=tcp
add action=redirect chain=dstnat dst-port=53 protocol=udp
/ip firewall service-port
set ftp disabled=yes
set tftp disabled=yes
set h323 disabled=yes
set sip disabled=yes
set pptp disabled=yes
/ip service
set telnet disabled=yes
set ftp disabled=yes
set ssh disabled=yes
set api disabled=yes
set api-ssl disabled=yes
/ipv6 address
add address=. from-pool=IPv6_Dimensione interface=bridge
/ipv6 dhcp-client
add interface=pppoe_dimensione pool-name=IPv6_Dimensione request=prefix use-peer-dns=no
/ipv6 firewall address-list
add address=::/128 comment="defconf: unspecified address" list=bad_ipv6
add address=::1/128 comment="defconf: lo" list=bad_ipv6
add address=fec0::/10 comment="defconf: site-local" list=bad_ipv6
add address=::ffff:0.0.0.0/96 comment="defconf: ipv4-mapped" list=bad_ipv6
add address=::/96 comment="defconf: ipv4 compat" list=bad_ipv6
add address=100::/64 comment="defconf: discard only " list=bad_ipv6
add address=2001:db8::/32 comment="defconf: documentation" list=bad_ipv6
add address=2001:10::/28 comment="defconf: ORCHID" list=bad_ipv6
add address=3ffe::/16 comment="defconf: 6bone" list=bad_ipv6
add address=fd12:672e:6f65:8899::/64 list=allowed
add address=fe80::/16 list=allowed
add address=ff02::/16 comment=multicast list=allowed
/ipv6 firewall filter
add action=accept chain=input comment="defconf: accept established,related,untracked" connection-state=established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=invalid
add action=accept chain=input comment="defconf: accept ICMPv6" protocol=icmpv6
add action=accept chain=input comment="defconf: accept UDP traceroute" port=33434-33534 protocol=udp
add action=accept chain=input comment="defconf: accept DHCPv6-Client prefix delegation." dst-port=546 protocol=udp src-address=fe80::/10
add action=accept chain=input comment="defconf: accept IKE" dst-port=500,4500 protocol=udp
add action=accept chain=input comment="defconf: accept ipsec AH" protocol=ipsec-ah
add action=accept chain=input comment="defconf: accept ipsec ESP" protocol=ipsec-esp
add action=accept chain=input comment="defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=input comment="defconf: drop everything else not coming from LAN" in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept established,related,untracked" connection-state=established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" connection-state=invalid
add action=drop chain=forward comment="defconf: drop packets with bad src ipv6" src-address-list=bad_ipv6
add action=drop chain=forward comment="defconf: drop packets with bad dst ipv6" dst-address-list=bad_ipv6
add action=drop chain=forward comment="defconf: rfc4890 drop hop-limit=1" hop-limit=equal:1 protocol=icmpv6
add action=accept chain=forward comment="defconf: accept ICMPv6" protocol=icmpv6
add action=accept chain=forward comment="defconf: accept HIP" protocol=139
add action=accept chain=forward comment="defconf: accept IKE" dst-port=500,4500 protocol=udp
add action=accept chain=forward comment="defconf: accept ipsec AH" protocol=ipsec-ah
add action=accept chain=forward comment="defconf: accept ipsec ESP" protocol=ipsec-esp
add action=accept chain=forward comment="defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=forward comment="defconf: drop everything else not coming from LAN" in-interface-list=!LAN
add action=accept chain=input comment="allow established and related" connection-state=established,related
add action=accept chain=input comment="accept ICMPv6" protocol=icmpv6
add action=accept chain=input comment="defconf: accept UDP traceroute" port=33434-33534 protocol=udp
add action=accept chain=input comment="accept DHCPv6-Client prefix delegation." dst-port=546 protocol=udp src-address=fe80::/16
add action=accept chain=input comment="allow allowed addresses" src-address-list=allowed
add action=drop chain=input
add action=accept chain=forward comment=established,related connection-state=established,related
add action=drop chain=forward comment=invalid connection-state=invalid log=yes log-prefix=ipv6,invalid
add action=drop chain=forward disabled=yes log-prefix=IPV6
/ipv6 nd
set [ find default=yes ] interface=bridge
/snmp
set contact= location=Network trap-generators=start-trap trap-interfaces=all trap-version=3
/system clock
set time-zone-name=Europe/Rome
/tool mac-server
set allowed-interface-list=LAN
/tool mac-server mac-winbox
set allowed-interface-list=LAN