log disconnessione del modem
Fri Sep 16 07:49:08 2022 daemon.info cwmpd[10647]: PROT_TRACE: Events are waiting, need to contact ACS
Fri Sep 16 07:49:08 2022 daemon.info cwmpd[10647]: CONNECTION: Connecting to server retry 1.
Fri Sep 16 07:49:08 2022 daemon.err cwmpd[10647]: UBUS_CLIENT: Failed to retrieve external IP address
Fri Sep 16 07:49:08 2022 daemon.err cwmpd[10647]: SOCK_TRACE: cwmp_createClientSocket - no ip to bind to on interface wwan - fail
Fri Sep 16 07:49:08 2022 daemon.crit cwmpd[10647]: CONNECTION: Failed to create socket.
Fri Sep 16 07:49:08 2022 daemon.info cwmpd[10647]: PROT_TRACE: Nb of retries 2
Fri Sep 16 07:49:08 2022 daemon.info cwmpd[10647]: PROT_TRACE: Min retry wait time 10
Fri Sep 16 07:49:08 2022 daemon.info cwmpd[10647]: PROT_TRACE: Max retry wait time 20
Fri Sep 16 07:49:08 2022 daemon.info cwmpd[10647]: PROT_TRACE: Effective retry wait time 10
Fri Sep 16 07:49:08 2022 daemon.info cwmpd[10647]: PROT_TRACE: LAST STATE: <Idle>
Fri Sep 16 07:49:08 2022 daemon.notice wansensing: (L2Sense) runs L2EntryExit.entry()
Fri Sep 16 07:49:08 2022 daemon.notice wansensing: (ethwan) runs worker_ethwan.check(network_interface_wan_ifdown)
Fri Sep 16 07:49:08 2022 daemon.warn wansensing: FRS -- Event : network_interface_wan_ifdown
Fri Sep 16 07:49:08 2022 daemon.warn wansensing: FRS Scenario : 0
Fri Sep 16 07:49:08 2022 daemon.notice wansensing: FRS -- WORKER Current Mode VDSL
Fri Sep 16 07:49:09 2022 user.notice mwan: ifdown interface iptv () <string_matching_support enabled>
Fri Sep 16 07:49:10 2022 user.notice mwan: ifdown interface wan () <string_matching_support enabled>
Fri Sep 16 07:49:13 2022 daemon.notice wansensing: (L2Sense) runs L2Main.check(timeout)
Fri Sep 16 07:49:14 2022 daemon.notice wansensing: WAN Sensing Mobile: 1
Fri Sep 16 07:49:16 2022 user.debug mmpbxd[9053]: [MMRVSIPIMPL::INTERFACESELECTION]:E: getProcessCb:370 - No process for action 4 on 0 mode
Fri Sep 16 07:49:16 2022 user.debug mmpbxd[9053]: [MMNETWORKSIP] :E: mmNetworkSipGetSubscriptionNotifier:7280 - MMPBX_ERROR_NOTSUPPORTED
Fri Sep 16 07:49:16 2022 user.debug mmpbxd[9053]: [MMRVSIPIMPL::NETWORKOBJ]:C: onStackLogEvent:2189 - SOCKET - RvSocketSendBuffer(sock=46,addr=5.97.171.107:5060,buf=0x1fd42c0,len=976,errno=22)=-2145371137
Fri Sep 16 07:49:16 2022 user.debug mmpbxd[9053]: [MMRVSIPIMPL::NETWORKOBJ]:C: onStackLogEvent:2189 - TRANSPORT - SipTransportUdpSendMessage - Message sending failed (crv=-1)
Fri Sep 16 07:49:16 2022 user.debug mmpbxd[9053]: [MMRVSIPIMPL::NETWORKOBJ]:C: onStackLogEvent:2189 - TRANSMITTER - TransmitterControlTransmitMessage - pTrx=0x0x201efc8: failed to send message 0x1f41f38 over UDP (Connection 0x(nil))(rv=-11:NETWORK_PROBLEM)
Fri Sep 16 07:49:16 2022 user.debug mmpbxd[9053]: [MMRVSIPIMPL::NETWORKOBJ]:C: onStackLogEvent:2189 - TRANSMITTER - ProcessAndTransmit - trx=0x0x201efc8: Message failed to be sent. (rv=-11)
Fri Sep 16 07:49:16 2022 user.debug mmpbxd[9053]: [MMRVSIPIMPL::NETWORKOBJ]:C: onStackLogEvent:2189 - TRANSMITTER - TransmitterControlSend - pTrx=0x0x201efc8: Failed to transmit message
Fri Sep 16 07:49:16 2022 user.debug mmpbxd[9053]: [MMRVSIPIMPL::NETWORKOBJ]:C: onStackLogEvent:2189 - TRANSACTION - TransactionTransportTrxStateChangeEv - pTransc=0x0x2059738: Message failed to be sent (rv=0:OK)
Fri Sep 16 07:49:16 2022 daemon.debug mmpbxfwctl[7722]: received cmd:iptables -t filter -C MMPBX --src 5.97.171.107 -p udp --dport 5060 -m comment --comment Allow_SIP -j ACCEPT
Fri Sep 16 07:49:16 2022 daemon.debug mmpbxfwctl[7722]: received cmd:iptables -t filter -D MMPBX --src 5.97.171.107 -p udp --dport 5060 -m comment --comment Allow_SIP -j ACCEPT &
Fri Sep 16 07:49:16 2022 user.debug mmpbxd[9053]: [MMNETWORKSIP] :E: mmNetworkSipGetSubscriptionNotifier:7280 - MMPBX_ERROR_NOTSUPPORTED
Fri Sep 16 07:49:16 2022 user.debug mmpbxd[9053]: [MMNETWORKSIP] :E: mmNetworkSipGetSubscriptionNotifier:7280 - MMPBX_ERROR_NOTSUPPORTED
Fri Sep 16 07:49:16 2022 user.info mmpbxd[9053]: SIP Registration: SIP: +390984502598 : Deregister
Fri Sep 16 07:49:16 2022 daemon.debug mmpbxfwctl[7722]: received cmd:iptables -t filter -D MMPBX --src 5.97.171.107 -p tcp --dport 5060 -m comment --comment Allow_SIP -j ACCEPT &
Fri Sep 16 07:49:18 2022 daemon.info cwmpd[10647]: PROT_TRACE: Events are waiting, need to contact ACS
Fri Sep 16 07:49:18 2022 daemon.info cwmpd[10647]: CONNECTION: Connecting to server retry 2.
Fri Sep 16 07:49:18 2022 daemon.err cwmpd[10647]: UBUS_CLIENT: Failed to retrieve external IP address
Fri Sep 16 07:49:18 2022 daemon.err cwmpd[10647]: SOCK_TRACE: cwmp_createClientSocket - no ip to bind to on interface wwan - fail
Fri Sep 16 07:49:18 2022 daemon.crit cwmpd[10647]: CONNECTION: Failed to create socket.
Fri Sep 16 07:49:18 2022 daemon.info cwmpd[10647]: PROT_TRACE: Nb of retries 3
Fri Sep 16 07:49:18 2022 daemon.info cwmpd[10647]: PROT_TRACE: Min retry wait time 20
Fri Sep 16 07:49:18 2022 daemon.info cwmpd[10647]: PROT_TRACE: Max retry wait time 40
Fri Sep 16 07:49:18 2022 daemon.info cwmpd[10647]: PROT_TRACE: Effective retry wait time 31
Fri Sep 16 07:49:18 2022 daemon.info cwmpd[10647]: PROT_TRACE: LAST STATE: <Idle>
Fri Sep 16 07:49:19 2022 daemon.notice wansensing: (L2Sense) runs L2Main.check(timeout)
Fri Sep 16 07:49:19 2022 daemon.notice wansensing: WAN Sensing Mobile: 1
Fri Sep 16 07:49:19 2022 user.debug mmpbxd[9053]: [MMRVSIPIMPL::REGTERMOBJ]:E: profileTimerCb:489 - no matching IP address, the registration will be aborted
Fri Sep 16 07:49:24 2022 daemon.notice wansensing: (L2Sense) runs L2Main.check(timeout)
Fri Sep 16 07:49:25 2022 daemon.notice wansensing: WAN Sensing Mobile: 1
Fri Sep 16 07:49:30 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:30 2022 daemon.notice wansensing: (L2Sense) runs L2Main.check(timeout)
Fri Sep 16 07:49:30 2022 daemon.notice wansensing: WAN Sensing Mobile: 1
Fri Sep 16 07:49:30 2022 daemon.notice igmpproxy[5307]: IGMP leave received from 192.168.1.103 on intf br-lan
Fri Sep 16 07:49:30 2022 daemon.notice igmpproxy[5307]: IGMP report received from 192.168.1.103 on intf br-lan
Fri Sep 16 07:49:30 2022 daemon.notice igmpproxy[5307]: Skipping local group received from 192.168.1.103 on intf br-lan
Fri Sep 16 07:49:31 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:32 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:33 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:35 2022 daemon.notice wansensing: (L2Sense) runs L2Main.check(timeout)
Fri Sep 16 07:49:36 2022 kern.warn kernel: [31075.455696] wl0: random key value: 7E14E29E6CAA9FC82260017F48C22A6ADC8CDFA9C64406B4B2E0F8E19FE7E0D5
Fri Sep 16 07:49:36 2022 daemon.notice hostapd: Deleting STA from monitor [36:c3:d8:5a:80:9f]
Fri Sep 16 07:49:36 2022 daemon.notice hostapd: Added new STA to monitor [36:c3:d8:5a:80:9f]
Fri Sep 16 07:49:36 2022 kern.warn kernel: [31075.524533] wl0: random key value: 154D44EE1D716C5028870258AD1265D04B63423C18050EAD5F9FCC0B3328432C
Fri Sep 16 07:49:36 2022 kern.warn kernel: [31075.525108] wl0: random key value: CC9DCECE54E0F4394B8A014CD19DB5754E95E2DF8FB00B8C4098AAA262BD9B57
Fri Sep 16 07:49:36 2022 daemon.info hostmanager: Ignoring wireless station disconnected event received from different access point
Fri Sep 16 07:49:36 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:36 2022 daemon.notice wansensing: WAN Sensing Mobile: 1
Fri Sep 16 07:49:36 2022 daemon.notice igmpproxy[5307]: IGMP leave received from 192.168.1.103 on intf br-lan
Fri Sep 16 07:49:36 2022 daemon.notice igmpproxy[5307]: IGMP report received from 192.168.1.103 on intf br-lan
Fri Sep 16 07:49:36 2022 daemon.notice igmpproxy[5307]: Skipping local group received from 192.168.1.103 on intf br-lan
Fri Sep 16 07:49:37 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:38 2022 kern.warn kernel: [31077.551726] wl0: random key value: D36D7F8CB7925CE5009A0316506412AA18F5EC8774EC0018CD3C593F18528DEE
Fri Sep 16 07:49:38 2022 daemon.info hostmanager: Probing device 36:c3:d8:5a:80:9f IP address 192.168.1.103 on interface br-lan
Fri Sep 16 07:49:38 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:38 2022 daemon.notice igmpproxy[5307]: IGMP leave received from 192.168.1.103 on intf br-lan
Fri Sep 16 07:49:38 2022 daemon.notice igmpproxy[5307]: IGMP report received from 192.168.1.103 on intf br-lan
Fri Sep 16 07:49:38 2022 daemon.notice igmpproxy[5307]: Skipping local group received from 192.168.1.103 on intf br-lan
Fri Sep 16 07:49:39 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:39 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:40 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:41 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:41 2022 daemon.notice wansensing: (L2Sense) runs L2Main.check(timeout)
Fri Sep 16 07:49:41 2022 daemon.notice wansensing: WAN Sensing Mobile: 1
Fri Sep 16 07:49:42 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:42 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:43 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:44 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:45 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:45 2022 daemon.err nanocdn-rr[8746]: ERROR mdnsT msg truncated on socket #4
Fri Sep 16 07:49:45 2022 daemon.err nanocdn-rr[8746]: ERROR mdnsT: msg truncated on socket #4
Fri Sep 16 07:49:46 2022 daemon.notice hostapd: Deleting STA from monitor [36:c3:d8:5a:80:9f]
Fri Sep 16 07:49:46 2022 daemon.notice wansensing: (L2Sense) runs L2Main.check(timeout)
Fri Sep 16 07:49:47 2022 daemon.notice wansensing: WAN Sensing Mobile: 1
Fri Sep 16 07:49:47 2022 daemon.info dnsmasq-dhcp[3925]: DHCPREQUEST(br-lan) 192.168.1.97 e2:e6:ef:c6:e6:80
Fri Sep 16 07:49:47 2022 daemon.info dnsmasq-dhcp[3925]: DHCPACK(br-lan) 192.168.1.97 e2:e6:ef:c6:e6:80
Fri Sep 16 07:49:47 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:48 2022 daemon.notice igmpproxy[5307]: IGMP leave received from 192.168.1.97 on intf br-lan
Fri Sep 16 07:49:48 2022 daemon.notice igmpproxy[5307]: IGMP report received from 192.168.1.97 on intf br-lan
Fri Sep 16 07:49:48 2022 daemon.notice igmpproxy[5307]: Skipping local group received from 192.168.1.97 on intf br-lan
Fri Sep 16 07:49:48 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:49 2022 daemon.info cwmpd[10647]: PROT_TRACE: Events are waiting, need to contact ACS
Fri Sep 16 07:49:49 2022 daemon.info cwmpd[10647]: CONNECTION: Connecting to server retry 3.
Fri Sep 16 07:49:49 2022 daemon.err cwmpd[10647]: UBUS_CLIENT: Failed to retrieve external IP address
Fri Sep 16 07:49:49 2022 daemon.err cwmpd[10647]: SOCK_TRACE: cwmp_createClientSocket - no ip to bind to on interface wwan - fail
Fri Sep 16 07:49:49 2022 daemon.crit cwmpd[10647]: CONNECTION: Failed to create socket.
Fri Sep 16 07:49:49 2022 daemon.info cwmpd[10647]: PROT_TRACE: Nb of retries 4
Fri Sep 16 07:49:49 2022 daemon.info cwmpd[10647]: PROT_TRACE: Min retry wait time 40
Fri Sep 16 07:49:49 2022 daemon.info cwmpd[10647]: PROT_TRACE: Max retry wait time 80
Fri Sep 16 07:49:49 2022 daemon.info cwmpd[10647]: PROT_TRACE: Effective retry wait time 60
Fri Sep 16 07:49:49 2022 daemon.info cwmpd[10647]: PROT_TRACE: LAST STATE: <Idle>
Fri Sep 16 07:49:49 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:50 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:51 2022 daemon.err nanocdn-rr[8746]: ERROR mdnsT msg truncated on socket #4
Fri Sep 16 07:49:51 2022 daemon.err nanocdn-rr[8746]: ERROR mdnsT: msg truncated on socket #4
Fri Sep 16 07:49:52 2022 daemon.notice wansensing: (L2Sense) runs L2Main.check(timeout)
Fri Sep 16 07:49:52 2022 daemon.notice wansensing: WAN Sensing Mobile: 1
Fri Sep 16 07:49:52 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:53 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:54 2022 daemon.notice igmpproxy[5307]: IGMP leave received from 192.168.1.1 on intf br-lan
Fri Sep 16 07:49:54 2022 daemon.notice igmpproxy[5307]: TO_IN report (group: 239.200.0.0, srcs: 0) received on intf br-lan
Fri Sep 16 07:49:54 2022 daemon.notice igmpproxy[5307]: Deleting host 192.168.1.1 from group 239.200.0.0 on intf br-lan
Fri Sep 16 07:49:54 2022 daemon.notice igmpproxy[5307]: Fast leave enabled on intf br-lan, deleting group 239.200.0.0
Fri Sep 16 07:49:54 2022 daemon.notice igmpproxy[5307]: Decremented EXCLUDE mode (0) for group 239.200.0.0 in membership DB
Fri Sep 16 07:49:54 2022 daemon.notice igmpproxy[5307]: Deleting group 239.200.0.0 in membership DB
Fri Sep 16 07:49:54 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:55 2022 daemon.err nanocdn-rr[8746]: ERROR mdnsT msg truncated on socket #4
Fri Sep 16 07:49:55 2022 daemon.err nanocdn-rr[8746]: ERROR mdnsT: msg truncated on socket #4
Fri Sep 16 07:49:55 2022 daemon.notice igmpproxy[5307]: IGMP report received from 192.168.1.1 on intf br-lan
Fri Sep 16 07:49:55 2022 daemon.notice igmpproxy[5307]: Adding new group 239.200.0.0 to list on intf br-lan
Fri Sep 16 07:49:55 2022 daemon.notice igmpproxy[5307]: Adding new group 239.200.0.0 to membership DB
Fri Sep 16 07:49:55 2022 daemon.notice igmpproxy[5307]: Adding new host 192.168.1.1 to list of group 239.200.0.0 on intf br-lan
Fri Sep 16 07:49:55 2022 daemon.notice igmpproxy[5307]: Updating IGMPv2 timer (260 sec) for group 239.200.0.0 on intf br-lan
Fri Sep 16 07:49:55 2022 daemon.notice igmpproxy[5307]: Switching group version to IGMPv2 for group 239.200.0.0 on intf br-lan
Fri Sep 16 07:49:55 2022 daemon.notice igmpproxy[5307]: IS_EX report (group: 239.200.0.0, srcs: 0) received on intf br-lan
Fri Sep 16 07:49:55 2022 daemon.notice igmpproxy[5307]: Decremented INCLUDE mode (0) for group 239.200.0.0 in membership DB
Fri Sep 16 07:49:55 2022 daemon.notice igmpproxy[5307]: Incremented EXCLUDE mode (1) for group 239.200.0.0 in membership DB
Fri Sep 16 07:49:55 2022 daemon.notice igmpproxy[5307]: Setting timer to GMI (260 sec) for group 239.200.0.0 on intf br-lan
Fri Sep 16 07:49:55 2022 daemon.notice igmpproxy[5307]: Filter mode change to EXCLUDE for group 239.200.0.0 in membership DB
Fri Sep 16 07:49:55 2022 daemon.notice igmpproxy[5307]: IGMP leave received from 192.168.1.164 on intf br-lan
Fri Sep 16 07:49:55 2022 daemon.notice igmpproxy[5307]: IGMP report received from 192.168.1.164 on intf br-lan
Fri Sep 16 07:49:55 2022 daemon.notice igmpproxy[5307]: Skipping local group received from 192.168.1.164 on intf br-lan
Fri Sep 16 07:49:55 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:55 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:56 2022 kern.crit kernel: [31095.648382] Line 0: xDSL G.994 training
Fri Sep 16 07:49:56 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:57 2022 daemon.notice wansensing: (L2Sense) runs L2Main.check(timeout)
Fri Sep 16 07:49:57 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:49:58 2022 daemon.err nanocdn-rr[8746]: ERROR mdnsT msg truncated on socket #4
Fri Sep 16 07:49:58 2022 daemon.err nanocdn-rr[8746]: ERROR mdnsT: msg truncated on socket #4
Fri Sep 16 07:49:58 2022 daemon.notice wansensing: WAN Sensing Mobile: 1
Fri Sep 16 07:49:59 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:50:01 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:50:01 2022 daemon.notice igmpproxy[5307]: IGMP report received from 192.168.1.1 on intf br-lan
Fri Sep 16 07:50:01 2022 daemon.notice igmpproxy[5307]: Updating IGMPv2 timer (260 sec) for group 239.200.0.0 on intf br-lan
Fri Sep 16 07:50:01 2022 daemon.notice igmpproxy[5307]: IS_EX report (group: 239.200.0.0, srcs: 0) received on intf br-lan
Fri Sep 16 07:50:01 2022 daemon.notice igmpproxy[5307]: Setting timer to GMI (260 sec) for group 239.200.0.0 on intf br-lan
Fri Sep 16 07:50:01 2022 daemon.notice igmpproxy[5307]: IGMP report received from 192.168.1.1 on intf br-lan
Fri Sep 16 07:50:01 2022 daemon.notice igmpproxy[5307]: Updating IGMPv2 timer (260 sec) for group 239.200.0.0 on intf br-lan
Fri Sep 16 07:50:01 2022 daemon.notice igmpproxy[5307]: IS_EX report (group: 239.200.0.0, srcs: 0) received on intf br-lan
Fri Sep 16 07:50:01 2022 daemon.notice igmpproxy[5307]: Setting timer to GMI (260 sec) for group 239.200.0.0 on intf br-lan
Fri Sep 16 07:50:02 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:50:03 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:50:03 2022 daemon.notice wansensing: (L2Sense) runs L2Main.check(timeout)
Fri Sep 16 07:50:03 2022 daemon.notice wansensing: WAN Sensing Mobile: 1
Fri Sep 16 07:50:04 2022 daemon.err generic_pnpd[6488]: send_new_device failed: /usr/bin/generic_pnpd:309:
Fri Sep 16 07:50:04 2022 kern.crit kernel: [31103.648236] Line 0: xDSL link down
Fri Sep 16 07:50:04 2022 daemon.notice wansensing: (L2Sense) runs L2Main.check(xdsl_0)
Fri Sep 16 07:50:05 2022 kern.crit kernel: [31104.648208] Line 0: ADSL G.992 started
Fri Sep 16 07:50:05 2022 daemon.notice wansensing: WAN Sensing Mobile: 1
Fri Sep 16 07:50:07 2022 daemon.notice wansensing: (L2Sense) runs L2Main.check(xdsl_0)
Fri Sep 16 07:50:07 2022 kern.crit kernel: [31106.648176] Line 0: xDSL link down
Fri Sep 16 07:50:07 2022 daemon.notice wansensing: WAN Sensing Mobile: 1
Fri Sep 16 07:50:08 2022 daemon.notice wansensing: (L2Sense) runs L2Main.check(timeout)
Fri Sep 16 07:50:08 2022 daemon.notice wansensing: WAN Sensing Mobile: 1
Fri Sep 16 07:50:11 2022 kern.crit kernel: [31110.648104] Line 0: xDSL G.994 training
Fri Sep 16 07:50:13 2022 daemon.notice wansensing: (L2Sense) runs L2Main.check(timeout)
Fri Sep 16 07:50:14 2022 daemon.notice wansensing: WAN Sensing Mobile: 1
Fri Sep 16 07:50:19 2022 daemon.notice wansensing: (L2Sense) runs L2Main.check(timeout)
Fri Sep 16 07:50:19 2022 daemon.notice wansensing: WAN Sensing Mobile: 1
Fri Sep 16 07:50:22 2022 kern.warn kernel: [31121.308445] jffs2: warning: (7010) jffs2_sum_write_data: Not enough space for summary, padsize = -725
Fri Sep 16 07:50:22 2022 kern.crit kernel: [31121.647895] Line 0: VDSL G.993 started
Fri Sep 16 07:50:23 2022 daemon.notice igmpproxy[5307]: Send IGMP packet to group 224.0.0.1 on intf br-lan
Fri Sep 16 07:50:23 2022 daemon.notice igmpproxy[5307]: IGMP query received from 192.168.1.1 on intf br-lan
Fri Sep 16 07:50:23 2022 daemon.notice igmpproxy[5307]: IGMP report received from 192.168.1.49 on intf br-lan
Fri Sep 16 07:50:23 2022 daemon.notice igmpproxy[5307]: Updating IGMPv2 timer (260 sec) for group 239.255.255.250 on intf br-lan
Fri Sep 16 07:50:23 2022 daemon.notice igmpproxy[5307]: IS_EX report (group: 239.255.255.250, srcs: 0) received on intf br-lan
Fri Sep 16 07:50:23 2022 daemon.notice igmpproxy[5307]: Setting timer to GMI (260 sec) for group 239.255.255.250 on intf br-lan
Fri Sep 16 07:50:23 2022 daemon.notice igmpproxy[5307]: IGMP report received from 192.168.1.42 on intf br-lan
Fri Sep 16 07:50:23 2022 daemon.notice igmpproxy[5307]: Skipping local group received from 192.168.1.42 on intf br-lan
Fri Sep 16 07:50:24 2022 daemon.notice igmpproxy[5307]: IGMP report received from 192.168.1.113 on intf br-lan
Fri Sep 16 07:50:24 2022 daemon.notice igmpproxy[5307]: Skipping local group received from 192.168.1.113 on intf br-lan
Fri Sep 16 07:50:24 2022 daemon.notice wansensing: (L2Sense) runs L2Main.check(timeout)
Fri Sep 16 07:50:24 2022 daemon.notice igmpproxy[5307]: IGMP report received from 192.168.1.1 on intf br-lan
Fri Sep 16 07:50:24 2022 daemon.notice igmpproxy[5307]: Updating IGMPv2 timer (260 sec) for group 239.200.0.0 on intf br-lan
Fri Sep 16 07:50:24 2022 daemon.notice igmpproxy[5307]: IS_EX report (group: 239.200.0.0, srcs: 0) received on intf br-lan
Fri Sep 16 07:50:24 2022 daemon.notice igmpproxy[5307]: Setting timer to GMI (260 sec) for group 239.200.0.0 on intf br-lan
Fri Sep 16 07:50:25 2022 daemon.notice wansensing: WAN Sensing Mobile: 1
Fri Sep 16 07:50:25 2022 daemon.notice igmpproxy[5307]: IGMP report received from 192.168.1.87 on intf br-lan
Fri Sep 16 07:50:25 2022 daemon.notice igmpproxy[5307]: Skipping local group received from 192.168.1.87 on intf br-lan
Fri Sep 16 07:50:26 2022 daemon.notice igmpproxy[5307]: IGMP report received from 192.168.1.1 on intf br-lan
Fri Sep 16 07:50:26 2022 daemon.notice igmpproxy[5307]: Skipping local group received from 192.168.1.1 on intf br-lan
Fri Sep 16 07:50:27 2022 daemon.notice igmpproxy[5307]: IGMP report received from 192.168.1.42 on intf br-lan
Fri Sep 16 07:50:27 2022 daemon.notice igmpproxy[5307]: Updating IGMPv2 timer (260 sec) for group 239.255.255.250 on intf br-lan
Fri Sep 16 07:50:27 2022 daemon.notice igmpproxy[5307]: IS_EX report (group: 239.255.255.250, srcs: 0) received on intf br-lan
Fri Sep 16 07:50:27 2022 daemon.notice igmpproxy[5307]: Setting timer to GMI (260 sec) for group 239.255.255.250 on intf br-lan
Fri Sep 16 07:50:30 2022 daemon.notice igmpproxy[5307]: IGMP report received from 192.168.1.113 on intf br-lan
Fri Sep 16 07:50:30 2022 daemon.notice igmpproxy[5307]: Updating IGMPv2 timer (260 sec) for group 239.255.255.250 on intf br-lan
Fri Sep 16 07:50:30 2022 daemon.notice igmpproxy[5307]: IS_EX report (group: 239.255.255.250, srcs: 0) received on intf br-lan
Fri Sep 16 07:50:30 2022 daemon.notice igmpproxy[5307]: Setting timer to GMI (260 sec) for group 239.255.255.250 on intf br-lan
Fri Sep 16 07:50:30 2022 daemon.notice wansensing: (L2Sense) runs L2Main.check(timeout)
Fri Sep 16 07:50:30 2022 daemon.notice wansensing: WAN Sensing Mobile: 1
Fri Sep 16 07:50:32 2022 daemon.notice igmpproxy[5307]: IGMP report received from 192.168.1.1 on intf br-lan
Fri Sep 16 07:50:32 2022 daemon.notice igmpproxy[5307]: Skipping local group received from 192.168.1.1 on intf br-lan
Fri Sep 16 07:50:35 2022 daemon.notice wansensing: (L2Sense) runs L2Main.check(timeout)
Fri Sep 16 07:50:36 2022 daemon.notice wansensing: WAN Sensing Mobile: 1
Fri Sep 16 07:50:37 2022 kern.crit kernel: [31136.647613] Line 0: VDSL G.993 channel analysis
Fri Sep 16 07:50:40 2022 daemon.notice igmpproxy[5307]: IGMP leave received from 192.168.1.164 on intf br-lan
Fri Sep 16 07:50:40 2022 daemon.notice igmpproxy[5307]: IGMP report received from 192.168.1.164 on intf br-lan
Fri Sep 16 07:50:40 2022 daemon.notice igmpproxy[5307]: Skipping local group received from 192.168.1.164 on intf br-lan
Fri Sep 16 07:50:41 2022 kern.crit kernel: [31140.216152] Line 0: VDSL2 link up, Bearer 0, us=21600, ds=129673
Fri Sep 16 07:50:41 2022 kern.crit kernel: [31140.216165] Line 0: VDSL2 link up, Bearer 1, us=0, ds=0
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.216179] bcmxtmcfg: ULS Port 0
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.216196] bcmxtmcfg: XTM Link Mode is VDSL G.inpRtx
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.216203] bcmxtmcfg:ulPhysPort[0] m_ulTrafficMonitorPort[4]
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.216211] bcmxtmcfg: XTM LinkInfo. P-0, S-UP(1), Service =PTM(2)
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.216218] bcmxtmcfg: ReconfSAR P-0, T-2
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.216225] bcmxtmcfg: TxPAF Status = Disabled
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.216236] bcmxtmcfg: ChkSILI Port = 0, BondingPort = 4
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.297214] Setting ADSL threshold to 512
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.305063] Setting VDSL threshold to 512
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.313143] Setting VDSL RTX threshold to 512
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.321224] Setting GFAST threshold to 512
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.445299] (SetConnCfg)Created new connection
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.671424] bcmxtmrt: TxPAF Status = Disabled
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.671440] bcmxtmrt: MAC address: a4 91 b1 b8 e8 6a
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.671446] bcmxtmrt: register_netdev
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.684446] bcmxtmrt: register_netdev done
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.684471] bcmxtmrt: netif_carrier_off
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.684482] BcmXdslWanDevIsUp: wanDevIsUp=1
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.684540] bcmxtmcfg: Reserve TxQueueIdx=0 for vcid 0
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.684554] bcmxtmcfg: Reserve TxQueueIdx=1 for vcid 0
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.684562] bcmxtmcfg: Reserve TxQueueIdx=2 for vcid 0
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.684569] bcmxtmcfg: Reserve TxQueueIdx=3 for vcid 0
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.684576] bcmxtmcfg: Reserve TxQueueIdx=4 for vcid 0
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.684583] bcmxtmcfg: Reserve TxQueueIdx=5 for vcid 0
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.684589] bcmxtmcfg: Reserve TxQueueIdx=6 for vcid 0
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.684597] bcmxtmcfg: Reserve TxQueueIdx=7 for vcid 0
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.684629] NON-CO4 DSLAM based operations for PTM CRC & ENET FCS.
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.684733]
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.684733] bcmxtmrt: Tx Q Size = 512
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.684744] bcmxtmrt: Egress TM Q 0 Setup. Buffering/Q - 512
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.684850] bcmxtmrt: Traffic Type is Non-bonded-2.
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.684913]
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.684913] bcmxtmrt: Tx Q Size = 512
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.684921] bcmxtmrt: Egress TM Q 1 Setup. Buffering/Q - 512
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.685009] bcmxtmrt: Traffic Type is Non-bonded-2.
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.685060]
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.685060] bcmxtmrt: Tx Q Size = 512
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.685068] bcmxtmrt: Egress TM Q 2 Setup. Buffering/Q - 512
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.685156] bcmxtmrt: Traffic Type is Non-bonded-2.
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.685204]
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.685204] bcmxtmrt: Tx Q Size = 512
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.685212] bcmxtmrt: Egress TM Q 3 Setup. Buffering/Q - 512
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.685300] bcmxtmrt: Traffic Type is Non-bonded-2.
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.685353]
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.685353] bcmxtmrt: Tx Q Size = 512
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.685361] bcmxtmrt: Egress TM Q 4 Setup. Buffering/Q - 512
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.685448] bcmxtmrt: Traffic Type is Non-bonded-2.
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.685557]
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.685557] bcmxtmrt: Tx Q Size = 512
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.685567] bcmxtmrt: Egress TM Q 5 Setup. Buffering/Q - 512
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.685658] bcmxtmrt: Traffic Type is Non-bonded-2.
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.685943]
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.685943] bcmxtmrt: Tx Q Size = 512
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.685954] bcmxtmrt: Egress TM Q 6 Setup. Buffering/Q - 512
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.686047] bcmxtmrt: Traffic Type is Non-bonded-2.
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.686098]
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.686098] bcmxtmrt: Tx Q Size = 512
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.686107] bcmxtmrt: Egress TM Q 7 Setup. Buffering/Q - 512
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.686196] bcmxtmrt: Traffic Type is Non-bonded-2.
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.686214] bcmxtmrt: netif_carrier_on
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.686230] bcmxtmcfg: Connection UP, LinkActiveStatus=0x1, US=21600000, DS=129673000
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.827493] netdev path : iptvptm0 -> ptm0
Fri Sep 16 07:50:41 2022 daemon.notice netifd: Interface 'iptv' is enabled
Fri Sep 16 07:50:41 2022 daemon.notice netifd: Interface 'iptv' is setting up now
Fri Sep 16 07:50:41 2022 daemon.notice igmpproxy[5307]: Address 10.10.10.2/255.255.255.252 created on intf iptvptm0
Fri Sep 16 07:50:41 2022 user.err dlnad: 296>No matching interface
Fri Sep 16 07:50:41 2022 user.err dlnad: 296>No matching interface
Fri Sep 16 07:50:41 2022 user.err dlnad: 296>No matching interface
Fri Sep 16 07:50:41 2022 user.err dlnad: 296>No matching interface
Fri Sep 16 07:50:41 2022 user.err dlnad: 296>No matching interface
Fri Sep 16 07:50:41 2022 daemon.debug dnsmasq[3925]: listening on iptvptm0(#52): 10.10.10.2 port 53
Fri Sep 16 07:50:41 2022 daemon.notice netifd: Interface 'iptv' is now up
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31140.948852] netdev path : wanptm0 -> ptm0
Fri Sep 16 07:50:41 2022 daemon.notice netifd: Interface 'wan' is enabled
Fri Sep 16 07:50:41 2022 daemon.notice netifd: Network device 'ptm0' link is up
Fri Sep 16 07:50:41 2022 daemon.notice igmpproxy[5307]: Intf iptvptm0 becomes upstream
Fri Sep 16 07:50:41 2022 daemon.notice igmpproxy[5307]: Add intf iptvptm0 as MRT virtual interface 1
Fri Sep 16 07:50:41 2022 daemon.notice netifd: 8021q 'iptvptm0' link is up
Fri Sep 16 07:50:41 2022 daemon.notice netifd: Interface 'iptv' has link connectivity
Fri Sep 16 07:50:41 2022 daemon.notice netifd: 8021q 'wanptm0' link is up
Fri Sep 16 07:50:41 2022 daemon.notice netifd: Interface 'wan' has link connectivity
Fri Sep 16 07:50:41 2022 daemon.notice netifd: Interface 'wan' is setting up now
Fri Sep 16 07:50:41 2022 daemon.notice igmpproxy[5307]: Subscribe all groups in membership DB on intf iptvptm0
Fri Sep 16 07:50:41 2022 daemon.notice igmpproxy[5307]: Join group 239.255.255.250 on intf iptvptm0
Fri Sep 16 07:50:41 2022 daemon.notice igmpproxy[5307]: Join group 239.200.0.0 on intf iptvptm0
Fri Sep 16 07:50:41 2022 kern.warn kernel: [31141.091403] [0;33;41m[ERROR mcast] bcm_mcast_netlink_process_snoop_cfg,926: interface 52 could not be found[0m
Fri Sep 16 07:50:41 2022 daemon.notice wansensing: (L2Sense) runs L2Main.check(timeout)
Fri Sep 16 07:50:41 2022 daemon.notice wansensing: WAN Sensing Mobile: 1
Fri Sep 16 07:50:42 2022 daemon.info pppd[26202]: Plugin connstate.so loaded.
Fri Sep 16 07:50:42 2022 daemon.info pppd[26202]: Plugin rp-pppoe.so loaded.
Fri Sep 16 07:50:42 2022 daemon.info pppd[26202]: RP-PPPoE plugin version 3.8p compiled against pppd 2.4.7
Fri Sep 16 07:50:42 2022 daemon.notice pppd[26202]: pppd 2.4.7 started by root, uid 0
Fri Sep 16 07:50:42 2022 daemon.notice pppd[26202]: Connection state changed to connecting (phase 2)
Fri Sep 16 07:50:42 2022 daemon.warn pppd[26202]: Read gracefulRestartPath = /etc/ppp/pppoesession_wanptm0, session=772 peerEth=88:a2:5e:17:89:4d
Fri Sep 16 07:50:42 2022 daemon.info pppd[26202]: Sent PADT
Fri Sep 16 07:50:42 2022 daemon.err bcmubusbridge[1904]: Can't delete the chain 'QoS_l2classify', it's referenced in chain 'POSTROUTING', rule 0.
Fri Sep 16 07:50:42 2022 daemon.notice igmpproxy[5307]: Add mfc entry src 81.74.224.78, group 239.200.0.0 from intf iptvptm0 to intf br-lan
Fri Sep 16 07:50:42 2022 user.notice mwan: ifup interface iptv (iptvptm0) <string_matching_support enabled>
Fri Sep 16 07:50:43 2022 daemon.debug dnsmasq[3925]: listening on ptm0(#51): fe80::a691:b1ff:feb8:e86a%ptm0 port 53
Fri Sep 16 07:50:43 2022 user.notice firewall: Reloading firewall due to ifup of iptv (iptvptm0)
Fri Sep 16 07:50:43 2022 user.notice pppoe-relay-tch: hotplug action=add device=wanptm0 bridge=lan
Fri Sep 16 07:50:43 2022 daemon.err dnsmasq[3925]: failed to send packet: Operation not permitted
Fri Sep 16 07:50:43 2022 user.notice pppoe-relay-tch: enabling relay via wanptm0 for bridge lan (br-lan)
Fri Sep 16 07:50:44 2022 daemon.err mcsnooper[4842]: mcpd msg 39 not supported
Fri Sep 16 07:50:44 2022 kern.info kernel: [31143.295139] device wanptm0 entered promiscuous mode
Fri Sep 16 07:50:44 2022 kern.info kernel: [31143.295156] device ptm0 entered promiscuous mode
Fri Sep 16 07:50:44 2022 kern.info kernel: [31143.315691] br-lan: port 7(wanptm0) entered forwarding state
Fri Sep 16 07:50:44 2022 kern.info kernel: [31143.315776] br-lan: port 7(wanptm0) entered forwarding state
Fri Sep 16 07:50:44 2022 daemon.err mcsnooper[4842]: mcpd msg 39 not supported
Fri Sep 16 07:50:46 2022 kern.info kernel: [31145.320434] br-lan: port 7(wanptm0) entered forwarding state
Fri Sep 16 07:50:46 2022 user.notice firewall: Reloading firewall due to ifupdate of iptv (iptvptm0)
Fri Sep 16 07:50:46 2022 daemon.notice wansensing: (L2Sense) runs L2Main.check(timeout)
Fri Sep 16 07:50:47 2022 daemon.err nanocdn-rr[8746]: ERROR mdnsT msg truncated on socket #4
Fri Sep 16 07:50:47 2022 daemon.err nanocdn-rr[8746]: ERROR mdnsT: msg truncated on socket #4
Fri Sep 16 07:50:47 2022 daemon.notice wansensing: (L2Sense) runs L2EntryExit.exit(VDSL,L3Sense)
Fri Sep 16 07:50:47 2022 daemon.notice wansensing: FRS OrigL2=L2: now activating the runtime function and the event for the worker
Fri Sep 16 07:50:47 2022 daemon.notice wansensing: FRS Timer-Interval: 30
Fri Sep 16 07:50:48 2022 daemon.notice wansensing: (L3Sense) runs L3EntryExit.entry(VDSL)
Fri Sep 16 07:50:49 2022 daemon.info cwmpd[10647]: PROT_TRACE: Events are waiting, need to contact ACS
Fri Sep 16 07:50:49 2022 daemon.info cwmpd[10647]: CONNECTION: Connecting to server retry 4.
Fri Sep 16 07:50:49 2022 daemon.err cwmpd[10647]: UBUS_CLIENT: Failed to retrieve external IP address
Fri Sep 16 07:50:49 2022 daemon.err cwmpd[10647]: SOCK_TRACE: cwmp_createClientSocket - no ip to bind to on interface wwan - fail
Fri Sep 16 07:50:49 2022 daemon.crit cwmpd[10647]: CONNECTION: Failed to create socket.
Fri Sep 16 07:50:49 2022 daemon.info cwmpd[10647]: PROT_TRACE: Nb of retries 5
Fri Sep 16 07:50:49 2022 daemon.info cwmpd[10647]: PROT_TRACE: Min retry wait time 80
Fri Sep 16 07:50:49 2022 daemon.info cwmpd[10647]: PROT_TRACE: Max retry wait time 160
Fri Sep 16 07:50:49 2022 daemon.info cwmpd[10647]: PROT_TRACE: Effective retry wait time 130
Fri Sep 16 07:50:49 2022 daemon.info cwmpd[10647]: PROT_TRACE: LAST STATE: <Idle>
Fri Sep 16 07:50:52 2022 daemon.info pppd[26202]: Sent PADT
Fri Sep 16 07:50:52 2022 daemon.info pppd[26202]: PPP session is 772
Fri Sep 16 07:50:52 2022 daemon.warn pppd[26202]: Connected to 88:a2:5e:17:89:4d via interface wanptm0
Fri Sep 16 07:50:52 2022 daemon.warn pppd[26202]: Write gracefulRestartPath = /etc/ppp/pppoesession_wanptm0, session=772 peerEth=88:a2:5e:17:89:4d
Fri Sep 16 07:50:52 2022 kern.warn kernel: [31151.492245] netdev path : ppp0 -> wanptm0 -> ptm0
Fri Sep 16 07:50:52 2022 kern.info kernel: [31151.492291] pppoe-wan: renamed from ppp0
Fri Sep 16 07:50:52 2022 daemon.notice igmpproxy[5307]: Intf ppp0 is deleted
Fri Sep 16 07:50:52 2022 daemon.info pppd[26202]: Renamed interface ppp0 to pppoe-wan
Fri Sep 16 07:50:52 2022 daemon.info pppd[26202]: Using interface pppoe-wan
Fri Sep 16 07:50:52 2022 daemon.notice pppd[26202]: Connect: pppoe-wan <--> wanptm0
Fri Sep 16 07:50:52 2022 daemon.notice pppd[26202]: Connection state changed to authenticating (phase 5)
Fri Sep 16 07:50:52 2022 daemon.notice pppd[26202]: PAP authentication succeeded
Fri Sep 16 07:50:52 2022 daemon.notice pppd[26202]: peer from calling number 88:A2:5E:17:89:4D authorized
Fri Sep 16 07:50:52 2022 daemon.notice pppd[26202]: Connection state changed to networking (phase 7)
Fri Sep 16 07:50:52 2022 daemon.notice igmpproxy[5307]: Address 87.1.76.156/255.255.255.255 created on intf pppoe-wan
Fri Sep 16 07:50:52 2022 daemon.notice igmpproxy[5307]: Address 87.1.76.156/32 has been deleted on intf pppoe-wan
Fri Sep 16 07:50:52 2022 daemon.notice igmpproxy[5307]: Address 87.1.76.156/255.255.255.255 created on intf pppoe-wan
Fri Sep 16 07:50:52 2022 daemon.notice igmpproxy[5307]: Intf pppoe-wan up
Fri Sep 16 07:50:52 2022 daemon.notice pppd[26202]: local IP address 87.1.76.156
Fri Sep 16 07:50:52 2022 daemon.notice pppd[26202]: remote IP address 192.168.100.1
Fri Sep 16 07:50:52 2022 daemon.notice pppd[26202]: primary DNS address 85.38.28.7
Fri Sep 16 07:50:52 2022 daemon.notice pppd[26202]: secondary DNS address 85.38.28.6
Fri Sep 16 07:50:52 2022 daemon.notice pppd[26202]: Connection state changed to connected (phase 8)
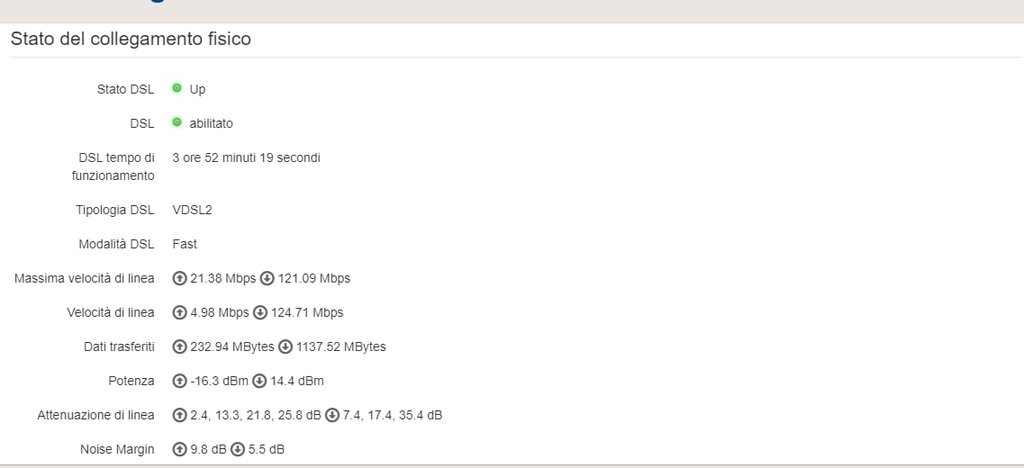
in allegato valori modem dopo 3h dall'ultima disconnessione: